Global ID Swiss: Biometric 3D Finger Vein Identification.

The term “biometric authentication” refers to the identification of people based on their bodily characteristics. Face recognition and fingerprint authentication are commonly used. The finger vein authentication technique, on the other hand, has lately gained a lot of interest as a novel biometric authentication method due to its high authentication accuracy when compared to existing biometric technologies.
Finger vein identification is a technique for identifying a person based on the vein pattern in their fingertips. Vein patterns appear as a series of black lines because deoxyhemoglobin in the blood absorbs near-infrared light. The picture of the finger vein patterns is captured using near-infrared lighting and a specific camera. After that, the picture is transformed into pattern data and saved as a template for biometric authentication data. During authentication, the picture of the user’s finger veins is recorded and compared to the user’s saved template.
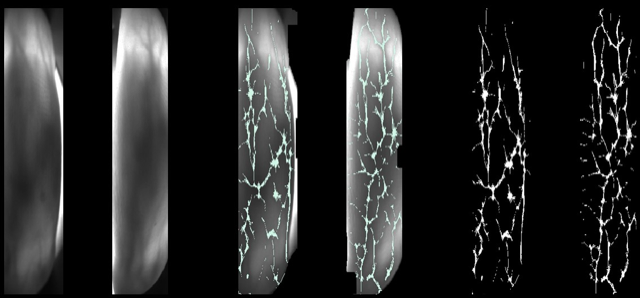
Global ID Swiss, a consortium of three Swiss laboratories, pioneered the use of 3D technology in finger vein recognition to address present and future biometric security concerns. This technique ensures the privacy of user data.

Founder of GLOBAL ID SA,[17] a spin-off of EPFL that brings this biometric identification technology to the market.[18]
The biometric technology based on vein recognition is considered ethical because the key is hidden and therefore impossible to steal. And the encryption is done end-to-end with a random code that changes constantly.[19] [20] [21]
Through our primary mandate of education and training in health care and other areas, FSF-IHCE partnership with Global ID, Global Digital Health Network and John Snow Inc aims to help minimize global cybercrime.
Educating employees and creating awareness to the public about their role in cybersecurity. And the impact it may have on human lives fosters a culture of security. In addition we aim to promoting technological innovations through training workshops that will enhance the security, accessibility, and long-term viability of data and information.
We hope that with your aid in the form of partnerships and donations, we will be able to provide training and raise awareness to help promote peace and minimize cyber conflicts in the digital space:
Cyber Security In Health Care.

When it comes to cyber security, the healthcare industry has always had a difficult time. It must strike a balance between its desire to help patients get better and the requirement to safeguard the very sensitive information generated by the treatment.
In 2015, there were over 750 data breaches, with the top seven exposing over 193 million personal details to fraud and identity theft. The health care sector has the top three data security breaches.
Anthem’s hack was the biggest in health care history. The hack exposed the personal details of 78.8 million current and former Anthem members and employees. Including names, birth dates, Social Security numbers, home addresses, and other personal information.
In 2015, the attacks continued. More than 11 million health-care records were compromised as a result of cyber-attacks in June 2016. According to a new report by Ponemon, a private research company, the average cost to health care organizations per compromised data is $355. Compared to $158 in other industries per lost or stolen record. For the 383 organizations that took part in the Ponemon study, the average overall cost of a data breach was $4 million. Given these figures, it’s clear that cyber and data security is a big problem in the health-care industry.
Because personal health information (PHI) is more valuable on the black market than many other forms of personally identifiable information, healthcare organizations have long been an appealing and profitable field for threat actors. This data is shared throughout the public health system. Which includes all public, commercial, and non-profit organizations that help offer vital public health services within a jurisdiction. As a result, cyber thieves are more likely to attack medical databases for financial/personal gain.
As a result of the COVID-19 pandemic, hospitals are implementing patient monitoring equipment such as vital-sign sensors in greater numbers than ever before. These patient monitoring gadgets may be utilized remotely and send vital information to medical professionals, allowing them to properly treat a patient’s needs. However, because of its increasingly networked and wireless nature, allowing devices to have remote access increases the attack surface.
Threats and vulnerabilities in cyberspace can compromise the confidentiality, availability, and integrity of IT networks and the medical equipment attached to them. If systems are hacked, a distributed denial-of-service (DDoS) attack might have catastrophic physical implications for patient care and lead to a loss of faith in healthcare providers.
Promoting Human Rights – International Humanitarian Law in Cyber Space.

It’s no surprise that governments, industry, and the technical community are focusing more on cybersecurity as attacks become more prevalent, complex, and severe. However, initiatives to improve cybersecurity frequently overlook or, worse, regard human rights as a barrier to cybersecurity. This is a risky and inaccurate assumption. It’s time to start addressing cybersecurity as a human rights issue.
Denial of access to information and its underlying infrastructure, such as network shutdowns, breaches a variety of rights, including the capacity of individuals to express themselves, freely gather and associate, and enjoy a variety of economic, social, and cultural rights.
There are several examples of information confidentiality being violated. Whether through financial data breaches, widespread government monitoring, or targeted attacks on human rights advocates or journalists. All in violation of the right to privacy, among other rights. Surveillance breaches of communication confidentiality have been connected to serious human rights abuses such as imprisonment, torture, and extrajudicial murders. The monitoring of Saudi dissident Omar Abdulaziz, which contributed to the arbitrary killing of Saudi journalist Jamal Khashoggi, is one example of a particularly heinous situation.
The risks associated with cyber security vulnerabilities will only rise as more people and devices become interconnected. Unfortunately, governments are either not focusing cybersecurity talks on human rights. Or, worse, are using cybersecurity as a pretext to increase internet control.
Cyber Security on Humanitarians.
Information is the driving force behind humanitarian aid. Information influences priorities and resource allocation from early warnings through needs assessments to final evaluations. Furthermore, a crisis motivates individuals to collect and share personal information that they would not ordinarily disclose. Such as the names of missing family members, medical issues and needs, and their present and previous whereabouts. Indeed, the humanitarian principle of impartiality, which requires that help be given only on the basis of need, necessitates this knowledge.
Healthcare systems are becoming more digitalized and networked, yet they are frequently unsecured, making them highly vulnerable to cyber-attacks. Water and electricity infrastructure, as well as hospitals, are frequently destroyed by shelling in armed conflict. And services are only partially or not operating at all: picture a big cyber attack on top of that! This has the potential to be disastrous. Civilians caught up in war and violence are already battling hard enough without having their problems worsened.
Partners Section:




